Cybersecurity Training and Certification
Cybersecurity Training and Certification is designed to boost your team’s cybersecurity skills and knowledge. We offer specialized training and certification for corporate teams, government bodies, and military personnel, helping your organization stay ahead of cyber threats.

What we offer?
Our program provides thorough cybersecurity education, from basic principles to advanced threat detection and response. Training is delivered via a mix of advanced learning systems and practical simulations, using platforms like STM Academy and HackingDept. This combination of theory and hands-on practice ensures a comprehensive learning experience.
Achieve Success with Us
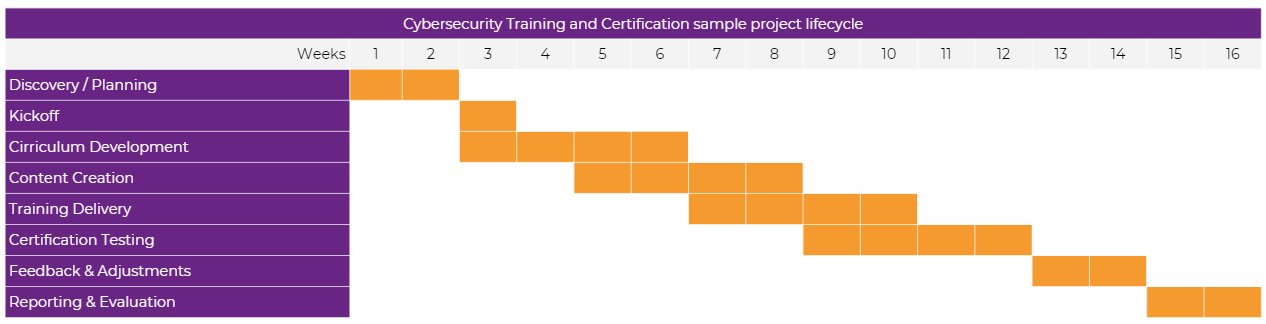
The process begins with a needs assessment to tailor the training to your organization’s specific needs. Our team of experts then creates a customized training plan. Participants engage in interactive sessions, hands-on exercises, and real-world simulations. After completing the program, participants receive certifications to validate their skills. This training not only improves individual capabilities but also strengthens your organization’s overall security culture, making your defenses more resilient against cyber threats.
Cybersecurity Training and Certification
Security of Web Applications
Network and Infrastructure Security
Application Security for Developers
Introduction to Red Teaming
C Code Analysis and Local Exploitation
Introduction to Malware Analysis
Essential Security
Mobile Applications
HackingDept Laboratory (Box/Cloud)
Security of Web Applications
Learn about the hidden risks in online activities and solidify your understanding through practical exercises.
Network and Infrastructure Security
Application Security for Developers
Analyze vulnerabilities in Java, .NET, and PHP application code, understand their exploitation, and learn best practices for secure coding.
Introduction to Red Teaming
Simulate cybercriminal attacks, social engineering tactics, and tool usage through targeted scenarios.
C Code Analysis and Local Exploitation
Learn Linux security basics, reverse-engineer C programs, and exploit vulnerabilities for privilege escalation and remote code execution.
Introduction to Malware Analysis
Learn to analyze malware, track API calls, decrypt network traffic, bypass certificate pinning, and identify Indicators of Compromise (IoCs) using static and dynamic methods.
Essential Security
Understand cybersecurity from an attacker’s perspective, covering basic hacking tools, Linux communication, and penetration testing, including command execution and vulnerability assessment.
Mobile Applications
Explore Android and iOS platforms, focusing on common programming errors and vulnerabilities in mobile operating systems that can affect user security without direct interaction with sensitive apps.
HackingDept Laboratory (Box/Cloud)
Access a virtual lab simulating a corporation’s telecommunications and application infrastructure, featuring over twenty virtual machines and physical network devices.
Cybersecurity Training and Certification
Security of Web Applications
Digitization has allowed us to transfer many aspects of our lives to the Internet, but it has brought with it a number of new threats. One small programmer error can expose users to harm and generate multi-million losses for the company. During our training, participants will learn in an accessible way the processes invisible to the human eye that happen when, for example, we order a transfer, log in to an office or look for a recipe on a forum, and the risks associated with them. Additionally, practical exercises prepared by our specialists will allow you to thoroughly consolidate the acquired knowledge.
Security of Web Applications
Digitization has allowed us to transfer many aspects of our lives to the Internet, but it has brought with it a number of new threats. One small programmer error can expose users to harm and generate multi-million losses for the company. During our training, participants will learn in an accessible way the processes invisible to the human eye that happen when, for example, we order a transfer, log in to an office or look for a recipe on a forum, and the risks associated with them. Additionally, practical exercises prepared by our specialists will allow you to thoroughly consolidate the acquired knowledge.
Security of Web Applications
Digitization has allowed us to transfer many aspects of our lives to the Internet, but it has brought with it a number of new threats. One small programmer error can expose users to harm and generate multi-million losses for the company. During our training, participants will learn in an accessible way the processes invisible to the human eye that happen when, for example, we order a transfer, log in to an office or look for a recipe on a forum, and the risks associated with them. Additionally, practical exercises prepared by our specialists will allow you to thoroughly consolidate the acquired knowledge.
Security of Web Applications
Digitization has allowed us to transfer many aspects of our lives to the Internet, but it has brought with it a number of new threats. One small programmer error can expose users to harm and generate multi-million losses for the company. During our training, participants will learn in an accessible way the processes invisible to the human eye that happen when, for example, we order a transfer, log in to an office or look for a recipe on a forum, and the risks associated with them. Additionally, practical exercises prepared by our specialists will allow you to thoroughly consolidate the acquired knowledge.
Security of Web Applications
Digitization has allowed us to transfer many aspects of our lives to the Internet, but it has brought with it a number of new threats. One small programmer error can expose users to harm and generate multi-million losses for the company. During our training, participants will learn in an accessible way the processes invisible to the human eye that happen when, for example, we order a transfer, log in to an office or look for a recipe on a forum, and the risks associated with them. Additionally, practical exercises prepared by our specialists will allow you to thoroughly consolidate the acquired knowledge.
Security of Web Applications
Digitization has allowed us to transfer many aspects of our lives to the Internet, but it has brought with it a number of new threats. One small programmer error can expose users to harm and generate multi-million losses for the company. During our training, participants will learn in an accessible way the processes invisible to the human eye that happen when, for example, we order a transfer, log in to an office or look for a recipe on a forum, and the risks associated with them. Additionally, practical exercises prepared by our specialists will allow you to thoroughly consolidate the acquired knowledge.
Security of Web Applications
Digitization has allowed us to transfer many aspects of our lives to the Internet, but it has brought with it a number of new threats. One small programmer error can expose users to harm and generate multi-million losses for the company. During our training, participants will learn in an accessible way the processes invisible to the human eye that happen when, for example, we order a transfer, log in to an office or look for a recipe on a forum, and the risks associated with them. Additionally, practical exercises prepared by our specialists will allow you to thoroughly consolidate the acquired knowledge.
Security of Web Applications
Digitization has allowed us to transfer many aspects of our lives to the Internet, but it has brought with it a number of new threats. One small programmer error can expose users to harm and generate multi-million losses for the company. During our training, participants will learn in an accessible way the processes invisible to the human eye that happen when, for example, we order a transfer, log in to an office or look for a recipe on a forum, and the risks associated with them. Additionally, practical exercises prepared by our specialists will allow you to thoroughly consolidate the acquired knowledge.
Security of Web Applications
Digitization has allowed us to transfer many aspects of our lives to the Internet, but it has brought with it a number of new threats. One small programmer error can expose users to harm and generate multi-million losses for the company. During our training, participants will learn in an accessible way the processes invisible to the human eye that happen when, for example, we order a transfer, log in to an office or look for a recipe on a forum, and the risks associated with them. Additionally, practical exercises prepared by our specialists will allow you to thoroughly consolidate the acquired knowledge.
Project Team Composition
Our specialized project team includes experienced professionals with expertise in various areas of cybersecurity, ensuring a thorough and effective implementation of our training and certification programs:

- Project Manager (PM)
- Business Analyst
- Cybersecurity Trainer
- Certification Specialist
- E-learning Developer
- Simulation Platform Specialist


How We Can Power Your Industry




Experience Our Process
Transform your business with our Custom Workflow Automation Solution. We analyze your workflows, design tailored automation, and integrate it seamlessly into your systems. Enjoy thorough testing, smooth deployment, and added support including user training and documentation. Experience a new level of efficiency—contact us to get started today!